Scammers don’t wear ski masks anymore—they hide in your inbox and phone screen. Their goal? To swipe your data before you realize what’s missing. Protecting yourself isn’t rocket science; it’s habit-building. These strategies will outsmart digital tricksters before they ever get close. Ready to lock things down?
Turn On Multi-Factor Authentication For All Accounts

Your password, no matter how strong, can be easily stolen in a data breach. That’s why Multi-Factor Authentication (MFA) is essential. It requires a temporary code or biometric scan, which means a criminal needs both your password and your physical phone to log in. The extra step is the most powerful defense you have.
Secure Every Login With A Password Manager

It’s almost impossible to remember dozens of complex, unique passwords. A password manager handles it effortlessly by generating strong, distinct credentials for every website you use. It then securely stores and autofills them. This essential tool also ensures you never reuse a compromised password, instantly shielding all your accounts from attack.
Inspect Links Carefully Before Clicking

Before clicking anything in an unexpected email, always verify the true destination. Scammers use subtle fake links, but when you move your cursor over the text, it reveals the actual web address at the screen’s bottom. If that revealed URL doesn’t belong to the expected company, simply close the message and delete the email.
Keep Your Devices And Apps Fully Updated
Every software update release includes critical security patches designed to close vulnerabilities that hackers actively exploit. Neglecting these leaves a device exposed. Automating updates across your computer, phone, and apps is the easiest way to ensure these digital defenses are immediately installed, keeping your devices protected constantly.
Activate Real-Time Alerts For Account Activity
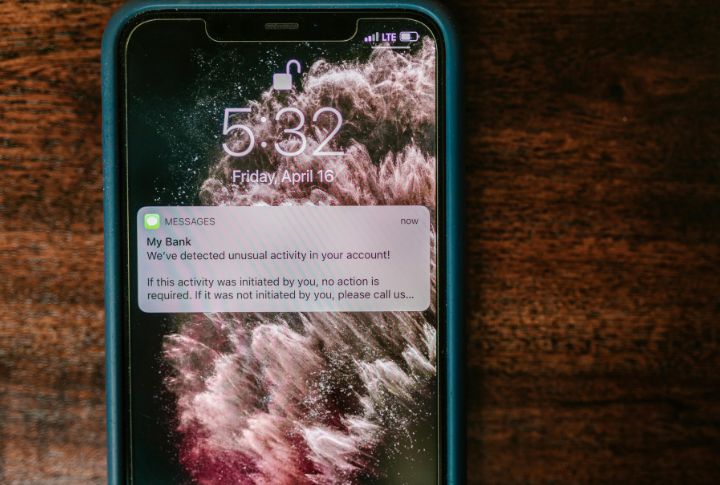
Financial security depends on speed. By enabling real-time alerts on your banking and credit card accounts, you get an immediate text or email notification the moment a suspicious transaction or unusual login occurs. This capability also allows you to confirm or shut down unauthorized activity within minutes and mitigate potential damage.
Limit Personal Information Shared Online

Online profiles are treasure maps for scammers; they collect small, public details—like job history or pet names—to use for verification questions or creating highly believable phishing schemes. Sharing less private information publicly and using alternate details if possible makes it much harder for criminals to compile enough data to impersonate or target you successfully.
Type Sensitive URLs Manually, Don’t Click Links

The simple, disciplined habit guarantees you bypass deceptive phishing links and typosquatting sites that aim to capture your credentials. When you receive an email prompting a login or account action, avoid clicking the link directly. Instead, open a new browser window and manually type the official website address yourself.
Use A VPN On Public Wi-Fi Networks

Public Wi-Fi, like in airports or coffee shops, is inherently unsecured, meaning your data travels unprotected. A quality VPN (Virtual Private Network) solves this by encrypting all your communication. It wraps your sensitive activity, like online banking, in an armored tunnel, shielding it from local snooping attempts by nearby criminals.
Scrutinize Unexpected Emails And Requests
If a company you know suddenly sends a strange, urgent request for a password or financial details, treat it as highly suspect. Look for telltale signs like grammatical errors or peculiar sender addresses. After all, legitimate businesses almost never ask for sensitive data in such a format. Always verify the request through an official phone number.
Back Up Important Data To A Secure Location

Ransomware attacks or sudden hardware failures can instantly wipe out years of irreplaceable files. This is why establishing a regular, automated backup routine—either to a secure cloud service or an external drive—is your safety net. If a disaster strikes, you simply restore your files and ensure the continuity of your digital life.